LDAPNightmare PoC Exploit: Impact on LSASS and Windows Domain Controller Stability
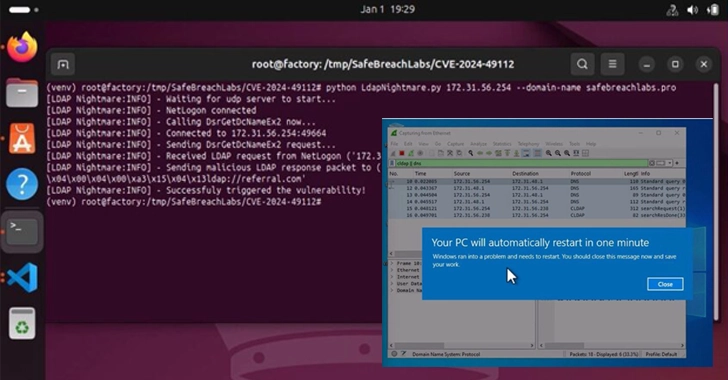
A new proof-of-concept (PoC) exploit has been released for a critical vulnerability affecting the Windows Lightweight Directory Access Protocol (LDAP), identified as CVE-2024-49113. This vulnerability can induce a denial-of-service (DoS) condition. Notably, the flaw received a CVSS score of 7.5 and was patched by Microsoft in December 2024 as part of its Patch Tuesday updates. This patch also addressed another significant vulnerability, CVE-2024-49112, which has a critical rating of 9.8 and could allow remote code execution.
The PoC, dubbed LDAPNightmare, was developed by SafeBreach Labs. It is designed to exploit the vulnerability by sending a DCE/RPC request to a target server, causing the Local Security Authority Subsystem Service (LSASS) to crash. The exploit requires that the victim’s Domain Controller (DC) be connected to the internet, which facilitates the attack by relaying a specially crafted CLDAP referral response packet.
Furthermore, SafeBreach Labs has determined that by modifying the CLDAP packet, the same exploit can potentially be used to execute remote code through the CVE-2024-49112 vulnerability. This indicates a severe risk for organizations that have not applied the recent security patches.
According to Microsoft, exploiting CVE-2024-49112 involves sending rogue RPC requests from untrusted networks to execute arbitrary code within the LDAP service context. Successful exploitation in the context of a domain controller necessitates attackers to send crafted RPC calls that trigger LDAP lookups against their domains.
To safeguard against these vulnerabilities, organizations are urged to apply the December patches without delay. In scenarios where immediate patching is infeasible, it is also recommended to implement monitoring systems to detect suspicious CLDAP referral responses, DsrGetDcNameEx2 calls, and DNS SRV queries related to these vulnerabilities.
For further technical details, visit the official Microsoft advisory on CVE-2024-49113.
Hudson Valley Host is premier provider of cutting-edge hosting solutions, specializing in delivering a seamless online experience for businesses and individuals. We offer a comprehensive range of hosting services, including Shared Hosting, VPS, Dedicated Servers, and Colocation. With 24/7 technical support, robust security measures, and user-friendly control panels, we empower clients in managing their online presence effortlessly. Hudson Valley Host is your trusted partner in achieving online success.
For Inquiries or to receive a personalized quote, please reach out to us through our contact form here or email us at sales@hudsonvalleyhost.com.










